Topic coverage
- AWS Management Tools
- AWS CloudWatch, AWS CloudTrail, AWS Config
- AWS Systems Manager, AWS Cost Management, AWS Free Tier,
- AWS Billing and Account Management, AWS Budgets, AWS Trusted Advisor
In our previous AWS tutorial, we discussed Amazon Databases. Now, we’ll discuss AWS Management Tools and explore the services they offer. What are AWS Management Tools? AWS Management Tools help users manage their cloud components and accounts. These tools allow provisioning, monitoring, and automating resources across the cloud.
Types of AWS Management Tools: There are four main categories of management tools integrated within AWS, ranging from EC2 to DynamoDB. These tools provide comprehensive control over cloud infrastructure.
- Provisioning: AWS CloudFormation lets you define and provision infrastructure resources using a template, ensuring secure and automated management. It helps maintain consistency by allowing only approved configurations.
- Monitoring: Amazon CloudWatch monitors AWS resources and applications, offering real-time insights into logs and metrics. It also triggers alerts based on resource changes.
- Operations Management: AWS Systems Manager allows centralized monitoring and automation of common tasks. AWS CloudTrail and Config enable activity logging and configuration tracking across resources.
- Managed Services: AWS OpsWorks manages configuration systems, integrating with Chef and Puppet for automation and maintenance.
Key AWS Management Tools Services:
- AWS CloudFormation: Simplifies cloud infrastructure management using templates to securely provision and model resources.
- AWS Service Catalog: Centralizes IT service management, enabling governance and compliance across AWS resources.
- Amazon CloudWatch: Provides system-wide visibility and performance monitoring of AWS resources.
- AWS Systems Manager: Offers operational insights, automates tasks, and allows centralized resource grouping for easier management.
- AWS CloudTrail: Tracks user activity and API usage, aiding in auditing and compliance.
- AWS Config: Monitors configuration changes and ensures compliance by tracking resource configurations.
- AWS OpsWorks: Automates server configuration and management using Chef and Puppet.
AWS Management Tools optimize cloud performance, reduce costs, and enhance security by following best practices. They provide real-time guidance and monitoring for efficient resource management.
AWS Cloud Watch
What is Amazon CloudWatch?
Amazon CloudWatch offers real-time monitoring of your AWS resources and applications running on the AWS platform. It allows you to collect and analyze metrics, which are measurable values related to the performance of your resources and applications.
On the CloudWatch dashboard, you’ll automatically see metrics for every AWS service you use. You can also build custom dashboards to track specific metrics for your applications, allowing for personalized monitoring based on your needs.
CloudWatch enables you to set alarms that trigger actions when certain thresholds are met. For example, if the CPU usage of an EC2 instance exceeds a specified limit, you can receive a notification or even automate the process of launching additional instances to manage the load. Similarly, it helps you identify under-utilized instances, allowing you to stop them and reduce costs. CloudWatch provides comprehensive visibility into resource usage, application performance, and overall system health.
Ways to access CloudWatch:
- Amazon CloudWatch Console: Visit the CloudWatch console at https://console.aws.amazon.com/cloudwatch/.
- AWS CLI: Use the AWS Command Line Interface for access (see the AWS CLI User Guide for setup instructions).
- CloudWatch API: Refer to the CloudWatch API Reference for more details.
- AWS SDKs: Check out the Tools for Amazon Web Services for more information on SDK access.
Amazon CloudWatch integrates with several services to enhance monitoring and automation:
- Amazon Simple Notification Service (SNS): Sends alerts to subscribed endpoints when CloudWatch alarms are triggered. Learn more in “Setting up Amazon SNS notifications.”
- Amazon EC2 Auto Scaling: Automatically scales EC2 instances based on demand, using CloudWatch alarms to adjust capacity. See “Dynamic Scaling” in the EC2 Auto Scaling guide for details.
- AWS CloudTrail: Tracks API calls made to CloudWatch, logging them to an S3 bucket for auditing. See “Logging CloudWatch API and console operations with CloudTrail.”
- AWS Identity and Access Management (IAM): Controls user access to AWS resources, ensuring secure authentication and authorization. See “Identity and access management for CloudWatch” for more information.
Open the CloudWatch console at https://console.aws.amazon.com/cloudwatch/.
The CloudWatch overview home page appears.
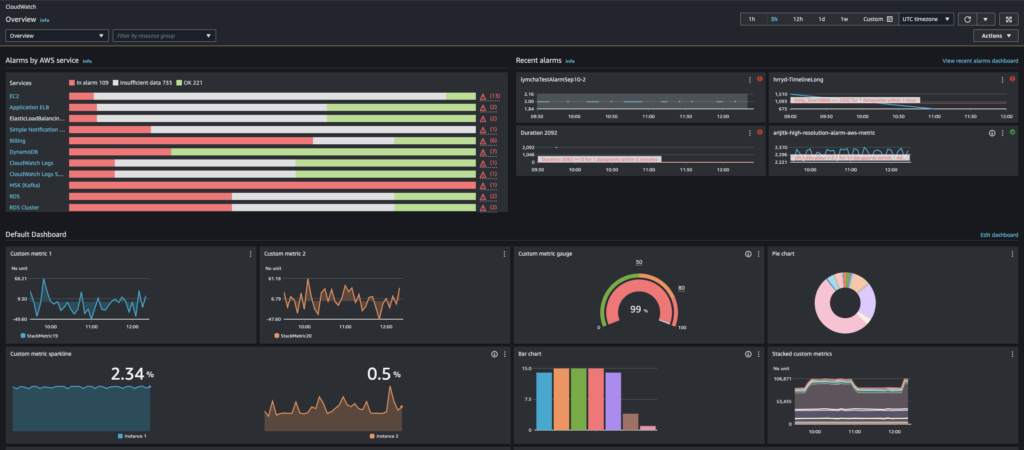
The overview provides an automatically refreshed display of key items:
- Alarms by AWS Service: Shows a list of AWS services used in your account, along with their alarm statuses. It highlights two or four alarms, depending on how many services are active. These alarms are either in the “ALARM” state or have recently changed state.
These top sections give a quick glance at the health of your AWS services by showing alarm statuses and any recent changes. This allows for efficient monitoring and issue diagnosis.
- Default Dashboard: If set up, a custom dashboard named CloudWatch-Default appears below the alarms. This dashboard lets you track metrics for custom services or applications, as well as important metrics from AWS services you wish to prioritize.
Note: The automatic dashboards only show data from the current account, even in cross-account monitoring setups. For creating cross-account dashboards, refer to “Creating a CloudWatch cross-account cross-Region dashboard.” From this overview, you can either view metrics across multiple AWS services or narrow down to specific resource groups or individual services, allowing focused monitoring of the resources you care about.
A Guide to Amazon CloudTrail
Introduction
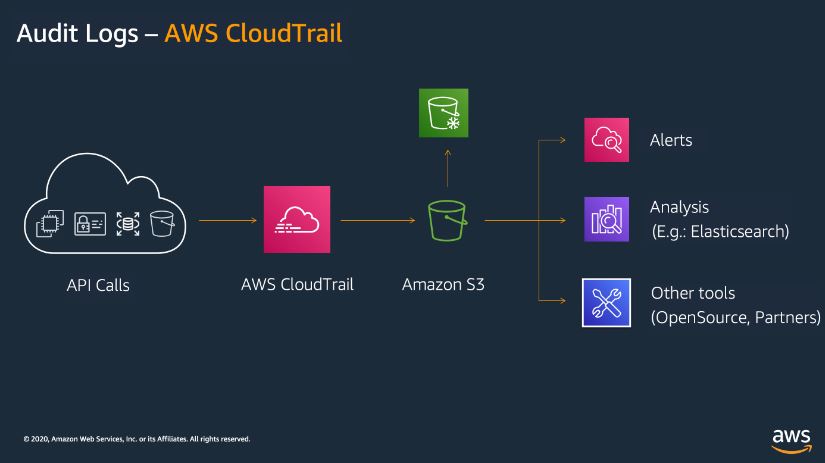
Amazon Web Services (AWS) provides numerous tools to help manage and maintain security, governance, and compliance across its vast ecosystem. One of the most pivotal services in this domain is Amazon CloudTrail. CloudTrail enables operational and risk auditing of your AWS account by recording and storing events related to user, role, and AWS service activities. These events cover actions taken in the AWS Management Console, AWS Command Line Interface (CLI), and AWS SDKs, ensuring thorough visibility into your account’s activity.
In this note, we will explore the fundamental aspects of CloudTrail, how it operates, its key features, and ways you can maximize its potential for auditing, compliance, and security.
What is Amazon CloudTrail?
Amazon CloudTrail is an AWS service designed to track and log all actions taken in your AWS account, providing operational insight and enabling comprehensive security monitoring. It records actions like API calls, resource modifications, or system events that occur within your AWS environment. By logging these activities, CloudTrail supports operational auditing, security governance, and compliance requirements, making it a crucial tool for any AWS-based system.
When you create an AWS account, CloudTrail is automatically enabled to record events related to resource access, management, and interactions. These records are known as CloudTrail events.
Key Features of CloudTrail
CloudTrail provides several ways to record events in your AWS account, including Event history, CloudTrail Lake, and Trails.
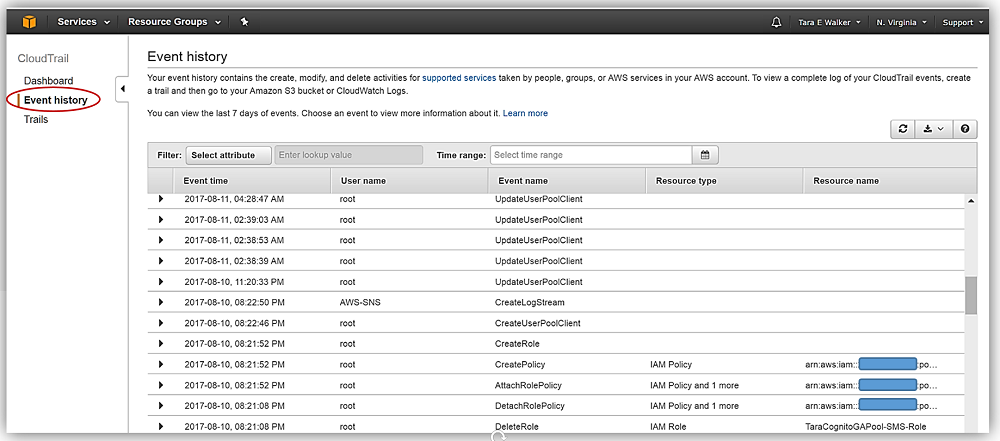
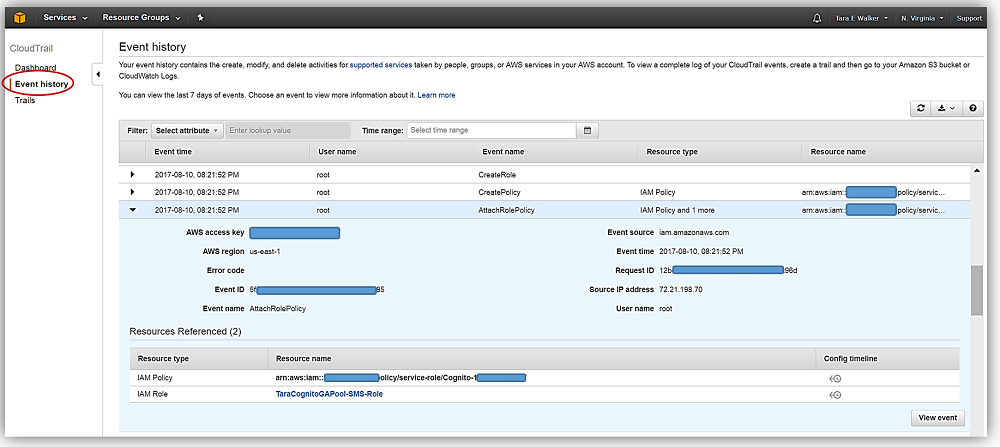
1. Event History
The Event history feature in CloudTrail offers a comprehensive and immutable record of all management events that occur within your AWS account. The event history is available for 90 days and can be searched, filtered, and downloaded for auditing purposes. Users can review historical data to investigate past account activities, ensuring they maintain a full grasp of what actions were taken, by whom, and when.
Notably, there are no costs associated with accessing or reviewing the Event history within CloudTrail.
Key capabilities of Event History include:
- Search and filter events using attributes such as user names, event times, or resource types.
- View, download, or archive events for future reference or further analysis.
- Maintain a secure log of actions without the need for additional configuration.
2. CloudTrail Lake
CloudTrail Lake is an extension of the standard CloudTrail service, acting as a managed data lake to capture, store, and analyze user and API activity on AWS. It provides advanced auditing capabilities and allows for more comprehensive and flexible queries of logged data. Events in CloudTrail Lake are stored in event data stores—specialized collections of logs that can be retained for up to 10 years.
CloudTrail Lake’s advantage lies in its ability to handle large-scale data while optimizing for fast retrieval. It converts events into Apache ORC format, a columnar storage format designed for performance efficiency. Users can choose different retention options based on their data governance needs, and it is possible to import previous logs from S3 into CloudTrail Lake for a more holistic view of past activity.
Features of CloudTrail Lake include:
- Advanced event selectors that help filter and aggregate event data according to specific criteria.
- Support for importing historical logs from S3.
- Dashboards for visualizing top trends in event data.
- Flexible retention periods—up to 10 years with the extended pricing option.
Costs are incurred for the ingestion and storage of events, and for querying stored data, making it essential to manage costs carefully when using CloudTrail Lake.
3. Trails
Trails offer a more granular way to record AWS activity by delivering event logs to designated Amazon S3 buckets. This approach allows for the integration of CloudTrail logs with other AWS services, such as CloudWatch Logs, Amazon EventBridge, and third-party security tools. You can create multiple trails for various purposes, like monitoring different AWS regions or accounts under an AWS Organization.
With Trails, users have the ability to detect and log Insights events, which analyze API calls for abnormal behavior in terms of call volumes and error rates. These events are invaluable for identifying security risks or operational issues.
When setting up trails, you have the option to:
- Select S3 buckets for storing logs.
- Enable encryption using AWS Key Management Service (KMS) keys.
- Configure notifications via Amazon SNS for log deliveries.
While the creation and delivery of trails to S3 are free, users are responsible for the S3 storage costs and any additional features they enable, such as encryption or third-party integration.
Benefits of Amazon CloudTrail
Visibility into AWS account activity is one of the primary benefits of CloudTrail. The service helps organizations maintain a clear picture of what is happening within their infrastructure, ensuring that they adhere to best practices in security, governance, and compliance.
1. Enhanced Security
By tracking API calls and resource interactions, CloudTrail ensures that you know exactly who is doing what within your AWS environment. This feature is vital for detecting unauthorized access or potential security threats. Combined with CloudWatch and EventBridge, CloudTrail helps create automated security responses to specific triggers.
2. Governance and Compliance
CloudTrail is an essential tool for meeting various regulatory and compliance standards, such as PCI-DSS, SOC 2, and GDPR. By providing a detailed audit trail of all AWS activity, it simplifies the process of demonstrating compliance during audits. The extended retention periods offered by CloudTrail Lake also support long-term data retention requirements.
3. Operational Monitoring
CloudTrail helps organizations monitor the health and efficiency of their AWS environment by providing insight into how resources are used and what actions are taken by different users or services. By logging these actions, businesses can optimize their operations, identify inefficiencies, and fine-tune permissions to minimize risk.
Accessing and Using CloudTrail
CloudTrail can be accessed through various interfaces, including:
1. CloudTrail Console
The CloudTrail console is a web-based interface that offers users an intuitive way to view and manage trails, event histories, and data lakes. Through the console, users can:
- Search and view event history.
- Download log files.
- Create and configure trails.
- Set up CloudTrail Lake data stores.
The console also allows users to manage the integration of CloudTrail logs with other AWS services like Amazon S3, CloudWatch, and EventBridge.
2. AWS CLI
For users who prefer command-line interaction, the AWS CLI provides a comprehensive set of commands for interacting with CloudTrail. This tool can be used to automate the management of trails, event data stores, and queries.
3. CloudTrail APIs
The CloudTrail APIs offer programmatic access to all the features available in CloudTrail, from creating trails to querying event logs. Developers can integrate these APIs into their applications to customize and automate their use of CloudTrail.
4. AWS SDKs
AWS SDKs allow developers to interact with CloudTrail through various programming languages, including Python, Java, .NET, and Node.js. The SDKs provide pre-built libraries for easy integration of CloudTrail’s features into applications, such as automated auditing tools or custom security dashboards.
How CloudTrail Works
At the core of CloudTrail’s functionality are events—records of interactions between AWS resources, users, or services. These events are logged as soon as actions are taken, ensuring near-real-time tracking of AWS activity.
CloudTrail logs are divided into two main categories:
- Management events, which track high-level resource interactions, such as creating or modifying an S3 bucket.
- Data events, which provide more granular details on specific actions, such as reading or writing data in an S3 object.
Best Practices for Using CloudTrail
To maximize the benefits of CloudTrail, it’s important to follow these best practices:
- Enable CloudTrail for all AWS accounts: Ensure that CloudTrail is enabled for every account in your organization to get a full view of all activity.
- Create multiple trails for different purposes: For large AWS deployments, create separate trails for different business units or regions to facilitate easier monitoring and reporting.
- Integrate CloudTrail with CloudWatch: Use CloudWatch alarms to notify you when suspicious or critical actions occur.
- Encrypt CloudTrail logs: Use AWS KMS to encrypt your CloudTrail logs to enhance the security of your stored data.
- Regularly review event history: Make it a routine practice to review the Event history in CloudTrail to identify any abnormal activity.
- Set up S3 bucket policies: Ensure that your CloudTrail logs stored in S3 are protected by strict access control policies to prevent unauthorized access.
Conclusion
Amazon CloudTrail is an indispensable tool for monitoring, securing, and managing AWS infrastructure. With its ability to track and log events in real-time, CloudTrail provides the insight and visibility required to maintain a secure and compliant AWS environment. Whether you are managing operational audits, meeting compliance requirements, or monitoring for security threats, CloudTrail ensures that you have the tools you need to stay in control of your AWS resources.
By following the best practices outlined in this webpage, you can ensure that CloudTrail is optimized to meet your auditing, security, and governance needs.
AWS Config
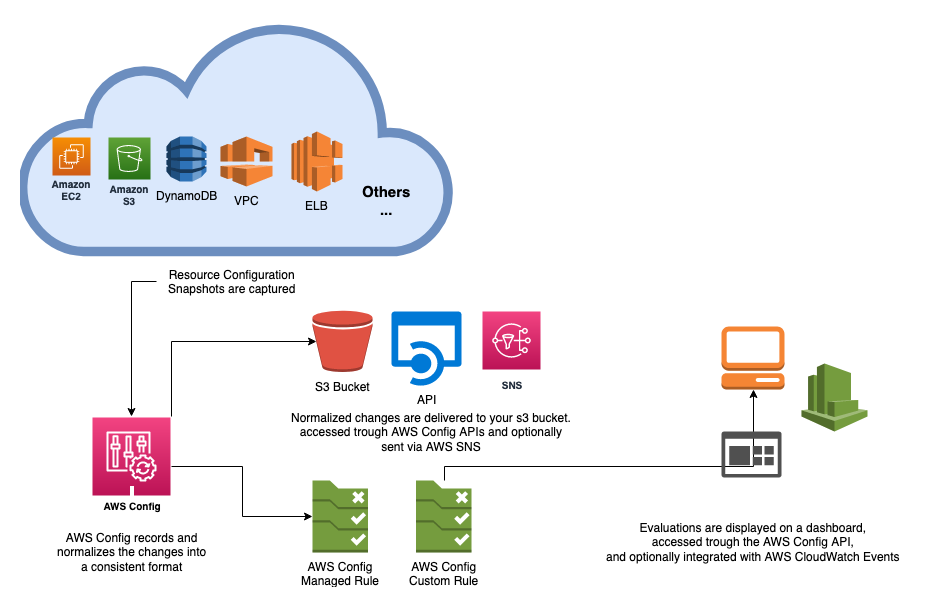
AWS Config is a fully managed service designed to help you manage AWS resources by providing an inventory, tracking configuration changes, and sending notifications to ensure security and governance. It allows you to monitor both current and deleted AWS resources, assess compliance with rules, and access configuration details for specific resources at any given time. This functionality supports tasks like auditing, security evaluations, tracking resource changes, and troubleshooting.
Overview
AWS Config offers a comprehensive view of your AWS resource configurations. This includes tracking how these resources are connected and configured over time. AWS Config defines a resource as any AWS entity, such as an Amazon EC2 instance, EBS volume, security group, or VPC. Upon activation, AWS Config scans your account for supported resources and creates a configuration item for each. Each configuration item offers a snapshot of the resource’s attributes, relationships, and any changes.
Whenever a resource’s configuration changes, AWS Config generates a new configuration item and maintains a historical record of changes since the configuration recorder was enabled. By default, AWS Config monitors all supported resources in a region, but you can customize it to track specific resource types if needed.
Organizations often need to assess risk and compliance statuses by reviewing configuration changes. AWS Config Rules allow users to define desired configurations for particular resources or entire AWS accounts. When changes are detected, AWS Config checks if they violate any rules and flags noncompliant resources, sending notifications via Amazon SNS.
AWS Config simplifies tracking configurations without requiring upfront infrastructure investment or complex agent management. Once enabled, AWS Config continuously updates the configuration data for all AWS resources in your account.
Use Cases
- Discovery: AWS Config discovers and records all resources in your account, including their configurations and any changes. Deleted resources are also retained, offering a full inventory of resources.
- Change Management: AWS Config tracks the creation, update, or deletion of resources and sends notifications for each configuration change. This includes the relationships between resources, allowing for an analysis of how changes to one resource impact others.
- Audit and Compliance: AWS Config and its Rules help organizations assess compliance with internal policies and regulatory standards by evaluating resource configurations against defined rules.
- Troubleshooting: AWS Config assists in troubleshooting operational issues by pinpointing recent configuration changes in affected resources.
- Security Analysis: By monitoring resource configurations, AWS Config helps identify potential security vulnerabilities. In case of a security incident, AWS Config allows you to review historical configurations to understand the resource’s state at any point in time.
Key Features
Previously, organizations had to manually track resource configurations and manage external databases for change tracking. AWS Config now automatically records and evaluates changes, presenting both the resource’s configuration and its compliance status in a dashboard.
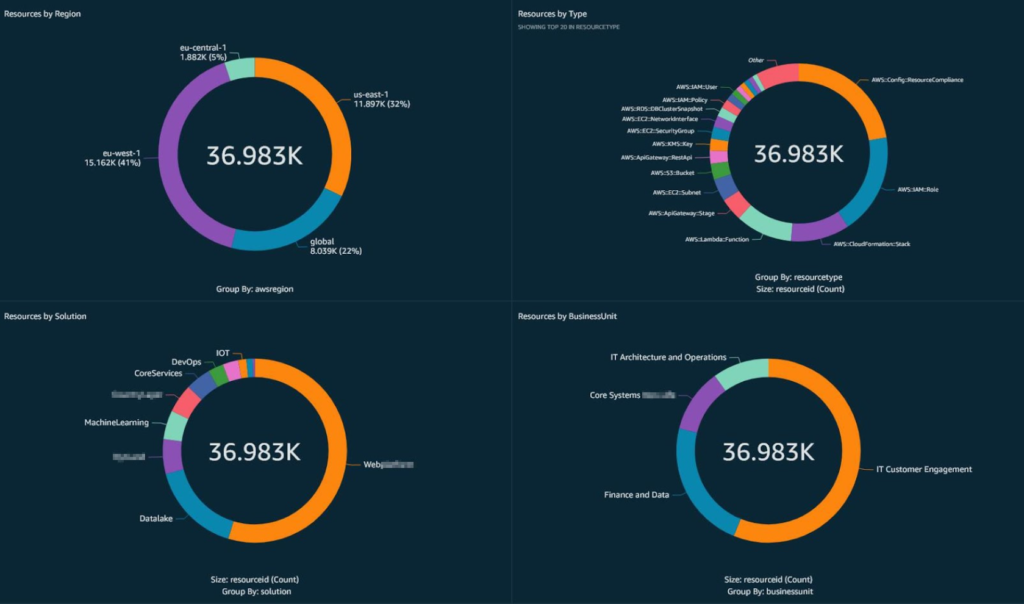
Fig-Summary of AWS Config resources
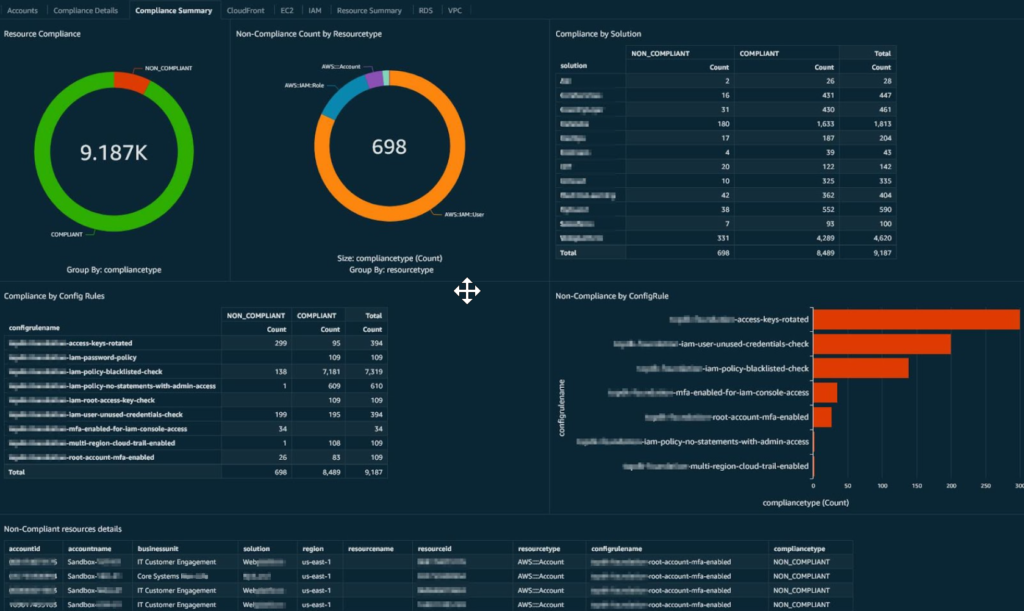
Figure : Summary of AWS Config resource compliance
AWS Config integrates with AWS CloudTrail to record API calls that trigger configuration changes, allowing you to trace who made changes, when, and from which IP address. AWS Config sends notifications when configuration or compliance changes occur, including details about old and new attributes. Additionally, AWS Config delivers configuration history files to an Amazon S3 bucket every six hours, providing a complete record of all configuration changes in your account.
By utilizing the AWS Management Console, API, or CLI, you can view resource configurations at any point in time and receive real-time updates on configuration and compliance changes.
Using AWS Config for security analysis and resource administration
AWS System Manager
What is AWS System Manager?
AWS Systems Manager is the operations hub for your AWS applications and resources and a secure end-to-end management solution for hybrid and multicloud environments that enables secure operations at scale.
Difference between Hybrid Cloud and Multicloud
Click here to know more on AWS System Manager
AWS Billing and Cost Management
What is AWS Billing and Cost Management?
AWS Trusted Advisor
AWS Trusted Advisor leverages insights gained from supporting over a million AWS customers to provide best practice recommendations. It evaluates your AWS environment to identify opportunities for cost savings, enhanced system availability, performance improvements, and security fixes. Users can monitor the overall health of their AWS resources and view potential savings through the AWS Trusted Advisor dashboard.
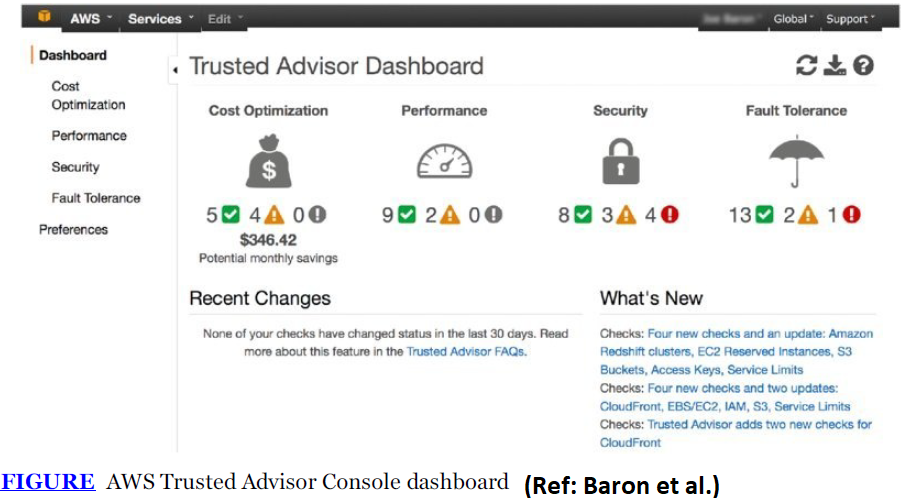
Accessible through the AWS Management Console, AWS Trusted Advisor can also be accessed programmatically via the AWS Support API. The service covers four key areas: cost optimization, security, fault tolerance, and performance. Dashboard statuses are color-coded to indicate the severity of the check:
- Red: Action required
- Yellow: Investigation suggested
- Green: No issues detected
Each check includes a detailed explanation, recommended actions, and helpful resources. All AWS customers receive four checks for free, which include:
- Service Limits: Alerts when usage exceeds 80% of a service limit, based on a snapshot.
- Security Groups – Specific Ports Unrestricted: Identifies security groups with open access (0.0.0.0/0) to certain ports.
- IAM Use: Reviews your use of AWS Identity and Access Management (IAM).
- MFA on Root Account: Warns if Multi-Factor Authentication (MFA) is not enabled on the root account.
Customers with Business or Enterprise Support plans can access over 50 checks. AWS Trusted Advisor also allows you to exclude non-relevant checks for specific resources, with the option to restore them later. It serves as a personalized cloud advisor, helping organizations optimize their resources based on best practices.
Summary :
AWS Trusted Advisor is a vital service that offers best practice recommendations to optimize AWS resources and services, helping users enhance performance, security, cost efficiency, and fault tolerance within their cloud environments. By following Trusted Advisor’s suggestions, organizations can reduce costs, improve system performance, and increase overall reliability. Trusted Advisor provides real-time, actionable guidance across five key areas: Cost Optimization, Performance, Security, Fault Tolerance, and Service Limits. In the Cost Optimization category, the service identifies underutilized, idle, or over-provisioned resources, such as EC2 instances with low CPU usage, and suggests cost-saving adjustments like rightsizing instances. The Performance category targets potential inefficiencies like unused EBS volumes or suboptimal RDS database instances, offering ways to enhance performance. On the security front, Trusted Advisor checks for vulnerabilities such as public access to S3 buckets or overly permissive security groups, helping users strengthen their AWS security posture. Additionally, the Fault Tolerance category highlights areas lacking redundancy, such as single Availability Zone databases or Elastic Load Balancers (ELBs) without failover, ensuring higher resilience and reliability. The Service Limits checks track usage against AWS service quotas, helping users stay within their limits and avoid potential disruptions.
Trusted Advisor compares its findings to AWS best practices, flagging areas for improvement and providing clear, actionable recommendations that users can implement to enhance their environment. By regularly reviewing Trusted Advisor’s findings and acting on its advice, organizations can ensure their AWS resources remain optimized and cost-effective, ultimately aligning their cloud infrastructure with AWS standards. Using the AWS Trusted Advisor dashboard, users can access a comprehensive overview of the checks performed across their AWS environment. The dashboard displays flagged checks in each category, details on specific issues, and cost-saving opportunities identified by Trusted Advisor. This provides a clear view of potential areas for optimization, enabling users to quickly take corrective action.
Users can also enable weekly email reports to receive Trusted Advisor’s key findings automatically. These reports summarize flagged checks, outline issues and recommendations, and estimate potential cost savings from resolving identified problems. To set this up, users can navigate to the “Preferences” section in the Trusted Advisor dashboard, select their reporting options, and start receiving regular updates on how to optimize their AWS environment.
Moreover, Trusted Advisor provides programmatic access through its API, allowing users to build custom tools for continuous monitoring and automated responses to its recommendations. To enable API access, users need to create an IAM policy with the necessary permissions, attach the policy to a new IAM role, and use that role to make Trusted Advisor API calls. This programmatic access empowers users to integrate Trusted Advisor’s recommendations into their automation scripts and tools, ensuring continuous alignment with AWS best practices. AWS CLI commands are also available for tasks such as listing Trusted Advisor checks, retrieving results, refreshing scans, and applying recommendations, making it easier to incorporate Trusted Advisor’s guidance into cloud management workflows. Through these features, AWS Trusted Advisor becomes a critical tool for optimizing cloud resources, improving efficiency, and maintaining best practices in the AWS ecosystem.
AWS Budget
What Are AWS Budgets?
AWS Budgets allows you to create customized budgets to monitor AWS costs and usage. Once configured, you can receive email notifications or SNS alerts when:
- Forecasted or actual costs or usage exceed the budget limit.
- Reserved Instances (RIs) or Savings Plans utilization falls below the desired level.
AWS Budget Actions enable you to set up automatic or manual responses when thresholds are surpassed, helping to control spending.
AWS Budgets integrates with several AWS services, such as:
- AWS Cost Explorer: Provides easy cost and usage analysis.
- AWS Chatbot: Delivers budget notifications to Slack channels or Amazon Chime.
- AWS Service Catalog: Tracks costs for approved AWS products.
Managing Your Costs with AWS Budgets
AWS Budgets allows the creation of various budget types:
- Cost: Set limits for expected expenditure on specific services.
- Usage: Monitor expected usage across services.
- RI Utilization: Track underutilized reserved instances.
- RI Coverage: Detect when fewer instances are covered by RIs.
- Savings Plan Utilization/Coverage: Monitor underutilized Savings Plans.
You can receive alerts when usage or costs approach, exceed, or fall below the set thresholds.
Budget Types:
- Fixed budget: Monitors a consistent budget across all periods.
- Planned budget: Adjusts for different amounts on a quarterly or monthly basis, up to a year.
- Auto-adjusted budget: Dynamically adjusts based on past usage or costs. Selecting the correct time range ensures accurate budget estimates and appropriate notifications.
Tutorial: Creating a Budget
To create a budget, start by selecting your monthly budget target. Use the AWS Budgets console to set up the budget to track overall spending, helping to prevent overspending across AWS services.
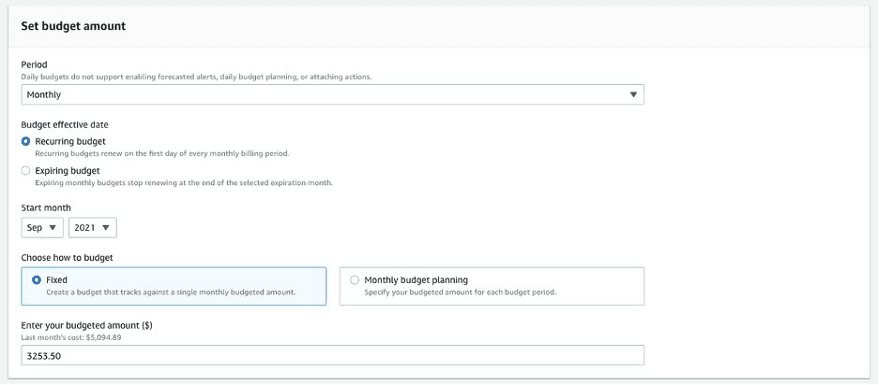
When configuring a budget, define:
- Period: Monthly
- Effective date: Recurring
- Budgeted amount: A predetermined value
You can apply scopes to target specific services, accounts, or regions, though a broad budget is helpful to catch overspending. Separate budgets can be created for specific teams or workloads, like development and testing.
It’s recommended to set two alert thresholds—at 50% and 75% of the budget amount—to balance monitoring and avoid notification fatigue.
Best Practices for AWS Budgets
- Use Managed Policies: AWS Budgets requires appropriate permissions to execute actions. AWS provides managed policies to ensure actions work correctly, including:
- User policy: Allows users to pass roles to the Budgets service.
- Budgets policy: Enables AWS Budgets to perform actions.
- Set Budget Alerts: You can send alerts to up to ten email addresses and one Amazon SNS topic per alert. Alerts can be based on actual or forecasted values:
- Actual alerts: Sent once the budget threshold is reached.
- Forecast alerts: Sent during a budget period when forecasted values exceed or fall below expectations.
AWS requires at least five weeks of data to create accurate budget forecasts.
- Control Access to AWS Budgets: To allow IAM users to create budgets, provide the necessary privileges, such as viewing billing information and creating SNS notifications. You can also set up programmatic access using the Budgets API by assigning specific IAM roles for controlled access.
AWS Budgets Summary
Improve planning and cost control with flexible budgeting and forecasting
Get started with AWS Budgets
Benefits:
- Custom budgets: Track your AWS costs, usage, and coverage by setting personalized budgets.
- Stay informed on usage: Receive alerts when costs or usage reach your set thresholds.
- Create custom actions: Automate actions based on budget performance to prevent overspending.
Use Cases:
- Monitor costs and usage: Keep track of your AWS expenses and resource utilization.
- Create scheduled reports: Generate regular reports to review your budget performance.
- Respond to thresholds: Set up notifications or actions when budget limits are exceeded.
- Here are 15 multiple-choice questions (MCQs) based on AWS Trusted Advisor:
- Which of the following areas is NOT covered by AWS Trusted Advisor?
a) Cost Optimization
b) Performance
c) Software Updates
d) Fault Tolerance - How can AWS Trusted Advisor be accessed?
a) Only through the AWS Management Console
b) Only via AWS CLI
c) Through both the AWS Management Console and AWS Support API
d) Through AWS CloudFormation - What color in the AWS Trusted Advisor dashboard indicates that action is required?
a) Red
b) Green
c) Yellow
d) Blue - Which of the following is one of the free AWS Trusted Advisor checks?
a) Idle EC2 Instances
b) MFA on Root Account
c) S3 Bucket Public Access
d) Fault Tolerance - What does the ‘Service Limits’ check in AWS Trusted Advisor alert users about?
a) Excessive API calls
b) Low RDS storage
c) Usage exceeding 80% of a service limit
d) Excessive EC2 usage costs - How many checks are available to AWS customers with Business or Enterprise Support plans?
a) 5
b) 20
c) 30
d) Over 50 - What kind of AWS Trusted Advisor status requires investigation but not immediate action?
a) Green
b) Red
c) Yellow
d) Orange - Which of the following is NOT a benefit provided by AWS Trusted Advisor?
a) Cost savings
b) Security improvements
c) Code refactoring
d) Performance optimization - What does AWS Trusted Advisor’s “IAM Use” check evaluate?
a) The number of EC2 instances
b) Whether MFA is enabled on the root account
c) The proper use of AWS Identity and Access Management (IAM) roles
d) Network latency - Which AWS Trusted Advisor check identifies security groups with unrestricted access to certain ports?
a) IAM Use
b) Service Limits
c) Security Groups – Specific Ports Unrestricted
d) RDS Performance - How can AWS Trusted Advisor’s API access be enabled?
a) By using AWS Lambda functions
b) By creating an IAM policy with the necessary permissions
c) By manually entering API keys into the console
d) By accessing AWS CloudFormation templates - Which check helps AWS users track usage against service quotas?
a) Cost Optimization
b) Fault Tolerance
c) Service Limits
d) Security Vulnerabilities - What feature of AWS Trusted Advisor helps users monitor their resources over time?
a) Dashboard color-coding
b) Weekly email reports
c) Custom Lambda functions
d) IAM role permissions - Which AWS Trusted Advisor check alerts users when certain ports have unrestricted access (0.0.0.0/0)?
a) Security Groups – Specific Ports Unrestricted
b) IAM Role Use
c) Service Limits
d) Root MFA - Which of the following can be used to integrate AWS Trusted Advisor’s recommendations into cloud management workflows?
a) AWS CloudFormation templates
b) AWS CLI commands
c) Amazon RDS snapshots
d) AWS OpsWorks configurations
Which AWS service allows you to create customized budgets to monitor costs and usage?
a) AWS Cost Explorer
b) AWS Budgets
c) AWS Billing Dashboard
d) AWS Pricing Calculator
Which type of budget allows you to track underutilized Reserved Instances (RIs)?
a) Cost Budget
b) Usage Budget
c) RI Utilization Budget
d) Savings Plan Budget
How can users receive alerts when forecasted or actual costs exceed a budget threshold?
a) Via email or Amazon SNS
b) By AWS CLI only
c) Through manual cost reports
d) AWS CloudFormation templates
What is the minimum amount of data required for AWS Budgets to create accurate cost forecasts?
a) 1 week
b) 3 weeks
c) 5 weeks
d) 6 months
Which AWS service provides detailed cost and usage analysis that integrates with AWS Budgets?
a) AWS Cost Explorer
b) AWS Lambda
c) AWS CloudTrail
d) Amazon S3
- Which AWS service enables infrastructure provisioning using templates?
- A) AWS CloudFormation
- B) AWS CloudTrail
- C) AWS Config
- D) AWS Systems Manager
- Which service provides real-time monitoring of AWS resources and applications?
- A) AWS CloudTrail
- B) Amazon CloudWatch
- C) AWS Config
- D) AWS OpsWorks
- What is the primary function of AWS CloudTrail?
- A) Provisioning resources
- B) Tracking user activity and API calls
- C) Automating server management
- D) Monitoring configuration changes
- Which AWS tool helps automate server configuration using Chef and Puppet?
- A) AWS OpsWorks
- B) AWS CloudFormation
- C) AWS Systems Manager
- D) AWS Budgets
- AWS CloudFormation falls under which management tool category?
- A) Monitoring
- B) Provisioning
- C) Operations Management
- D) Managed Services
- Which AWS service sends notifications when CloudWatch alarms are triggered?
- A) AWS Systems Manager
- B) Amazon SNS
- C) AWS CloudFormation
- D) AWS IAM
- AWS Identity and Access Management (IAM) controls which aspects of AWS resources?
- A) Authentication and Authorization
- B) Auditing and Compliance
- C) Monitoring and Metrics
- D) Resource Provisioning
- What can you use to automatically scale Amazon EC2 instances based on CloudWatch alarms?
- A) AWS Systems Manager
- B) Amazon SNS
- C) Amazon EC2 Auto Scaling
- D) AWS CloudTrail
- Which tool monitors configuration changes to AWS resources?
- A) AWS CloudTrail
- B) AWS Config
- C) AWS OpsWorks
- D) Amazon CloudWatch
- What does the AWS Trusted Advisor tool provide?
- A) Configuration management
- B) Real-time cost optimization recommendations
- C) User activity tracking
- D) Operational task automation
- Which tool allows for centralized operational insights and automation of routine tasks?
- A) AWS Systems Manager
- B) AWS CloudFormation
- C) AWS Budgets
- D) AWS Config
- What type of dashboard is displayed by default in Amazon CloudWatch?
- A) Cross-account dashboard
- B) CloudWatch-Default dashboard
- C) Custom resource dashboard
- D) AWS Management console dashboard
- Which AWS service provides comprehensive visibility into resource usage and performance?
- A) AWS CloudTrail
- B) AWS Systems Manager
- C) Amazon CloudWatch
- D) AWS Trusted Advisor
- In which AWS service can you create alarms to automatically trigger actions based on thresholds?
- A) AWS CloudTrail
- B) Amazon CloudWatch
- C) AWS Config
- D) AWS IAM
- What is the main benefit of using AWS OpsWorks?
- A) Real-time monitoring
- B) Automating server configuration and management
- C) API call tracking
- D) Infrastructure provisioning
- What is the primary purpose of Amazon CloudTrail?
- To manage billing and costs of AWS resources.
- To log and track user activity and API calls in AWS.
- To monitor server performance metrics.
- To configure AWS networking.
- How does Amazon CloudTrail assist in compliance and governance?
- By automating server management tasks.
- By providing detailed logs of user actions and system events.
- By reducing AWS resource costs.
- By automatically scaling AWS resources.
- Which feature of CloudTrail offers an immutable record of all management events for 90 days?
- CloudTrail Lake
- Trails
- Event History
- AWS Lambda
- What is one key feature of CloudTrail Lake?
- It automatically scales your AWS resources.
- It provides advanced auditing and querying capabilities.
- It generates random AWS events for testing.
- It only supports short-term event data storage.
- What is the role of CloudTrail Trails?
- To record events and deliver them to Amazon S3 buckets.
- To provide historical cost analysis.
- To manage AWS auto-scaling policies.
- To automatically backup all AWS services.
- Which of the following is NOT a key capability of CloudTrail’s Event History?
- Searching events by attributes like user names and resource types.
- Downloading and archiving events.
- Offering dashboards for visualizing trends.
- Providing an immutable record of past account activities.
- What can CloudTrail Lake store up to 10 years?
- Event History logs
- CloudWatch logs
- Event data stores
- S3 backup files
- What is a benefit of enabling CloudTrail across all AWS accounts in an organization?
- It reduces AWS billing costs.
- It provides complete visibility into all activities across the organization.
- It automatically enhances system performance.
- It reduces the need for AWS support tickets.
- Which of the following AWS services can be integrated with CloudTrail logs for enhanced monitoring?
- Amazon EC2
- Amazon CloudWatch
- Amazon RDS
- AWS Elastic Beanstalk
- How does CloudTrail support enhanced security in AWS environments?
- By scaling services automatically.
- By tracking API calls and resource interactions.
- By reducing AWS service costs.
- By enabling faster data transfer between regions.
- Which of the following is a recommended best practice for using CloudTrail?
- Use it only for specific AWS regions.
- Enable it for all AWS accounts in an organization.
- Store logs only on local servers.
- Do not integrate it with any other AWS service.
- How are CloudTrail logs categorized?
- Public and Private events
- Management and Data events
- Critical and Non-critical events
- Operational and Security events
- What is the benefit of encrypting CloudTrail logs using AWS KMS?
- To reduce the storage size of logs.
- To prevent unauthorized access to log data.
- To automatically delete logs after a certain period.
- To allow for easier integration with other services.
- Which of the following interfaces is NOT used to access CloudTrail?
- AWS CLI
- CloudTrail Console
- AWS SDKs
- AWS Auto Scaling
- What kind of events can be captured by CloudTrail’s Trails feature?
- Only user login activities
- Management and Data events
- Only system errors and warnings
- Network-related activities
AWS Config & System Manager
- What is AWS Config primarily designed to do?
a) Monitor network traffic
b) Manage AWS resources and track configuration changes
c) Optimize AWS costs
d) Automate security updates - Which of the following is not a feature of AWS Config?
a) Compliance assessment
b) Resource discovery
c) Change management
d) Data backup - AWS Config allows you to monitor which of the following?
a) Both current and deleted resources
b) Only current resources
c) Only EC2 instances
d) Only networking configurations - How does AWS Config notify users about configuration changes?
a) Through Amazon SES
b) Through Amazon SNS
c) Through AWS Lambda
d) Through AWS CloudWatch - What is a configuration item in AWS Config?
a) A log of EC2 usage
b) A snapshot of a resource’s attributes and changes
c) An Amazon S3 bucket
d) A billing report - How frequently does AWS Config deliver configuration history files to an Amazon S3 bucket?
a) Every 12 hours
b) Every 24 hours
c) Every 6 hours
d) Every 1 hour - Which AWS service does AWS Config integrate with to record API calls that trigger configuration changes?
a) AWS CloudTrail
b) AWS Lambda
c) AWS CloudWatch
d) Amazon SNS - AWS Config can be customized to track which of the following?
a) Only EC2 instances
b) Specific resource types
c) Only VPC configurations
d) AWS billing details - What is the purpose of AWS Config Rules?
a) To automate billing
b) To define desired configurations for resources
c) To update EC2 instance types
d) To enable auto-scaling - What type of resources does AWS Config monitor by default?
a) All supported resources in a region
b) Only networking resources
c) Only storage-related resources
d) None, until configured - What is AWS Systems Manager primarily used for?
a) Database management
b) Secure end-to-end management of AWS applications and resources
c) Network optimization
d) Monitoring billing costs - What are the two environments that AWS Systems Manager supports?
a) Single cloud and hybrid cloud
b) Hybrid cloud and multicloud
c) On-premises and public cloud
d) Private cloud and public cloud - Which of the following components is part of AWS Systems Manager’s operations management capabilities?
a) SSM Agent
b) OpsCenter
c) IAM
d) RDS - Which of the following is a category in AWS Systems Manager’s capabilities?
a) Data analysis
b) Node management
c) Security management
d) Resource tagging - Which agent performs actions on managed nodes in AWS Systems Manager?
a) AWS Config Agent
b) SSM Agent
c) EC2 Management Agent
d) IAM Policy Agent - What does AWS Systems Manager use to verify a user’s permissions before performing an action?
a) CloudFormation
b) Amazon S3
c) AWS IAM
d) AWS RDS - How does AWS Systems Manager provide operational insights into resources?
a) Through automated billing reports
b) Through artifacts such as OpsItems and incidents
c) By monitoring network traffic
d) By analyzing EC2 usage patterns - Which AWS service does AWS Config send configuration history files to for storage?
a) Amazon RDS
b) Amazon S3
c) AWS Lambda
d) Amazon DynamoDB - What kind of changes does AWS Config track for resources?
a) Changes in cost optimization
b) Creation, updates, and deletion of resources
c) Only creation and deletion of EC2 instances
d) Resource scaling events - What does AWS Config provide to help troubleshoot operational issues?
a) Detailed billing reports
b) Resource snapshots and change history
c) Automated server backups
d) EC2 instance performance analytics