Topics Covered
Overview of AWS Global Infrastructure
AWS Shared Responsibility Model,
AWS Identity and Access Management (IAM)
IAM Users, Groups, and Policies,
IAM Roles
IAM Best Practices
AWS Global Infrastructure: The Backbone of Cloud Excellence
Introduction
Welcome to the ultimate resource on AWS Global Infrastructure! AWS offers the most secure, extensive, and reliable global cloud infrastructure for all your applications. This guide provides an overview of the AWS Global Infrastructure, its key components, and the unparalleled benefits it offers.
AWS Global Regions
AWS has 33 launched Regions, each with multiple Availability Zones (AZs). There are 105 Availability Zones, with plans for 21 more AZs and seven more AWS Regions in Malaysia, Mexico, New Zealand, the Kingdom of Saudi Arabia, Thailand, Taiwan, and the AWS European Sovereign Cloud. AWS Regions are separate geographic areas that consist of multiple, physically separated, and isolated Availability Zones connected with low latency, high throughput, and highly redundant networking.
AWS Availability Zones (AZs)
An Availability Zone (AZ) is one or more discrete data centers with redundant power, networking, and connectivity in an AWS Region. AZs enable customers to operate production applications and databases that are more highly available, fault-tolerant, and scalable than would be possible from a single data center.
Key Points:
- AWS Regions typically consist of 3 or more Availability Zones.
- Each AZ comprises clusters of data centers with independent and redundant power, infrastructure, networking, and connectivity.
- Data centers within an AZ can house 50,000 to 80,000 servers.
- AZs are connected over distances ranging from 10 to 100 kilometers.
AWS Edge Locations
AWS provides various networking and content delivery services to ensure your data is transmitted securely and quickly across the globe. Edge networking services (Edge Locations) keep your data safe within the AWS global network, away from the risks of the open internet. Services like Amazon CloudFront, AWS Global Accelerator, and Amazon Route 53 are positioned worldwide to deliver your data with minimal latency, using high-speed, redundant fiber connections.
Key Points:
- AWS Edge Locations are strategically positioned points in the AWS network optimized for low-latency content delivery.
- There are over 600 CloudFront Points of Presence (POPs) and 13 Regional Edge Caches globally.
AWS Data Centers
AWS data centers are designed for security and reliability. They are distributed across Regions and AZs to ensure high availability and fault tolerance. Each data center is built with independent power, cooling, and physical security and is connected via redundant, ultra-low-latency networks.
Why Data Centers Matter:
- Data centers centralize and streamline equipment management.
- They provide backup power supplies for power outages.
- Data replication across several machines ensures disaster recovery.
- Temperature-controlled facilities extend equipment life.
- Security measures comply with data laws.
For more details, visit AWS Data Centers.
Network Architecture
AWS’s network architecture includes Virtual Private Clouds (VPCs), Direct Connect, and Transit Gateway. These components provide secure and scalable connectivity options for AWS customers, enabling them to build robust, high-performance applications.
Key Components:
- Virtual Private Clouds (VPCs): Virtual networks resembling traditional networks, with subnets for deploying AWS resources.
- Subnets: Ranges of IP addresses within a VPC, residing in a single Availability Zone.
Security and Compliance
AWS provides a comprehensive suite of security services and features to ensure data protection, meet compliance requirements, and protect against cybersecurity threats. AWS infrastructure Regions meet the highest levels of security, compliance, and data protection standards.
Benefits of AWS Global Infrastructure
The benefits of AWS Global Infrastructure include:
- Scalability: Easily scale applications to meet demand.
- Flexibility: Deploy applications in multiple Regions and AZs.
- High Availability: Ensure applications are always available.
- Disaster Recovery: Recover quickly from failures.
- Global Reach: Deploy applications closer to end-users for improved performance.
- Low Latency: Deliver data with minimal delay.
Conclusion
AWS Global Infrastructure provides a secure, extensive, and reliable cloud platform for all your applications. Its global reach and robust architecture ensure high availability, fault tolerance, and low latency. Explore the limitless possibilities with AWS Global Infrastructure and transform your business today.
AWS Shared Responsibility Model: Understanding Security Responsibilities
When considering the security of your data and applications, it’s essential to understand the AWS Shared Responsibility Model. This model defines the division of security responsibilities between AWS and its customers, differing significantly from traditional on-premises data centers.
Security in the Cloud vs. On-Premises Data Centers
Shift in Security Responsibilities:
On-Premises:
- In a traditional data center, you are responsible for managing all aspects of security. This includes physical security, network security, and the security of your data and applications. Every layer, from the hardware to the software, requires your attention and resources.
Cloud:
- In a cloud environment, such as AWS, security responsibilities are shared between you and AWS. This division allows you to focus more on your business needs rather than the underlying infrastructure.
AWS Responsibilities:
AWS is responsible for securing the underlying infrastructure that supports the cloud. This includes:
- Physical security of data centers.
- Network infrastructure security, ensuring that the network and systems are robust against external threats.
- Hardware security, managing and maintaining the physical servers and storage devices.
- Environmental security, including fire suppression, climate control, and power management.
Your(Customer) Responsibilities:
As an AWS customer, you are responsible for securing anything you put on the cloud or connect to the cloud. This encompasses:
- Data encryption and protecting data at rest and in transit.
- Application security, ensuring that your software is secure and free from vulnerabilities.
- Access management, controlling who can access your AWS resources and what actions they can perform.
- Operating system management, including updates and patches for any operating systems running on your AWS instances.
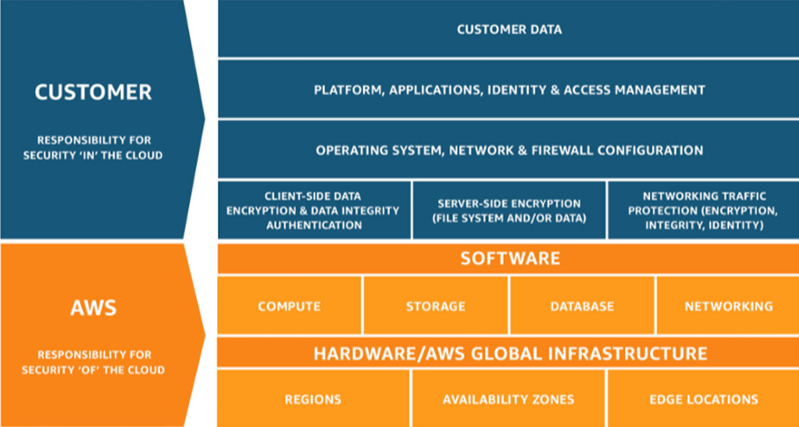
Advantages of the Shared Responsibility Model
Operational Burden Reduction:
One of the primary benefits of the Shared Responsibility Model is the reduction in operational burden. By allowing AWS to handle the security of the infrastructure, you can:
- Reduce the workload on your IT staff, enabling them to focus on more critical tasks.
- Lower costs associated with maintaining physical security and hardware.
Improved Security Posture:
The model also offers the potential for an improved security posture:
- AWS provides robust, industry-leading security measures by default, which you can leverage without needing to implement them yourself.
- Enhanced default security can be achieved with fewer actions required on your part.
Visual Representation: Inherited Controls vs Customer Control
Inherited Controls:
Inherited controls are those that customers fully inherit from AWS. These are aspects of security managed entirely by AWS, ensuring the foundational elements are secure without customer intervention. Examples include:
- Physical controls, such as security guards, cameras, and access management at data centers.
- Environmental controls, like climate control, fire suppression systems, and power management.
Shared Controls:
Shared controls are those that apply to both the infrastructure layer (managed by AWS) and the customer layers, but in different contexts. In these cases, AWS provides the requirements and infrastructure security, while you must implement your own controls within your use of AWS services. Examples include:
- Patch Management:
- AWS: Responsible for patching and fixing flaws within the infrastructure.
- Customer: Responsible for patching their guest operating system (OS) and applications running on AWS.
- Configuration Management:
- AWS: Maintains the configuration of its infrastructure devices.
- Customer: Responsible for configuring their own guest OS, databases, and applications.
- Awareness & Training:
- AWS: Trains its employees on security practices.
- Customer: Must train their own employees on how to use AWS services securely.
Customer Specific Controls:
Customer-specific controls are solely the responsibility of the customer. These controls are based on the specific applications and data you deploy within AWS services. Examples include:
- Service and Communications Protection:
- You may need to route or zone your data within specific security environments to meet your organization’s security policies.
- Zone Security:
- You must ensure that data is protected appropriately based on its classification and the compliance requirements of your industry.
Conclusion
The AWS Shared Responsibility Model offers a clear framework for understanding security roles in the cloud. By leveraging AWS’s robust infrastructure security measures, you can reduce operational burdens and enhance your security posture. However, it is crucial to remember that securing your applications, data, and operating systems remains your responsibility. Proper implementation of shared and customer-specific controls ensures that your cloud environment is as secure as possible. This model enables you to focus more on innovation and business growth while relying on AWS’s expertise to maintain a secure infrastructure
Introduction to AWS Identity and Access Management (IAM)
AWS Identity and Access Management (IAM) is a powerful service that allows you to control access to AWS resources securely. IAM enables you to manage users and their permissions, ensuring that only authorized individuals can access specific resources.
Key Features of IAM
User Management
IAM allows you to create individual user accounts for people within your organization. Each user can have their own credentials (password, access keys) and permissions. This means you can:
- Create and manage users: Add users to your AWS account and manage their permissions.
- Assign unique credentials: Each user can have a unique username and password, as well as access keys for programmatic access.
Group Management
Groups in IAM let you assign permissions to multiple users simultaneously. By organizing users into groups based on their roles or functions, you can:
- Simplify permissions management: Assign permissions to a group, and all users in that group inherit those permissions.
- Efficiently manage user access: Make changes to a group’s permissions without needing to update each user individually.
Role Management
IAM roles allow you to delegate permissions to different AWS resources or users without sharing long-term credentials. Roles are particularly useful for:
- Cross-account access: Allowing users or services in one AWS account to access resources in another account.
- Temporary access: Granting permissions to users, applications, or services for a limited time using temporary security credentials.
Policy Management
IAM policies define what actions are allowed or denied for users, groups, and roles. Policies are written in JSON and can be:
- Managed policies: Predefined policies provided by AWS that cover common use cases.
- Customer managed policies: Custom policies that you create and manage within your AWS account.
IAM Best Practices
Follow the Principle of Least Privilege
Always give users the minimum level of access necessary to perform their tasks. This reduces the risk of accidental or malicious changes to your AWS resources.
Enable Multi-Factor Authentication (MFA)
Enhance the security of your AWS account by enabling MFA. This requires users to provide two forms of authentication, typically something they know (password) and something they have (MFA device).
Regularly Review Permissions
Periodically review the permissions granted to users, groups, and roles to ensure they are still appropriate. Remove any unnecessary permissions to maintain a secure environment.
Use IAM Roles for Applications
Instead of embedding access keys in your applications, use IAM roles. This approach provides temporary security credentials, reducing the risk of long-term credentials being compromised.
Monitor IAM Activity
Enable AWS CloudTrail to log all IAM activity in your account. This allows you to monitor changes and access patterns, helping you detect and respond to suspicious activities.
Benefits of IAM
Enhanced Security
IAM provides fine-grained access control, allowing you to secure your AWS resources effectively. By managing who can access what, you reduce the risk of unauthorized access.
Scalability
As your organization grows, IAM scales with you. You can easily add new users, manage groups, and assign roles without compromising security.
Cost-Effective
IAM is a free service within AWS. You can implement robust security measures without additional costs, making it a cost-effective solution for managing access to your resources.
Compliance
IAM helps you meet regulatory and compliance requirements by providing detailed control over access to your resources. You can audit and review permissions, ensuring that only authorized individuals have access to sensitive data.


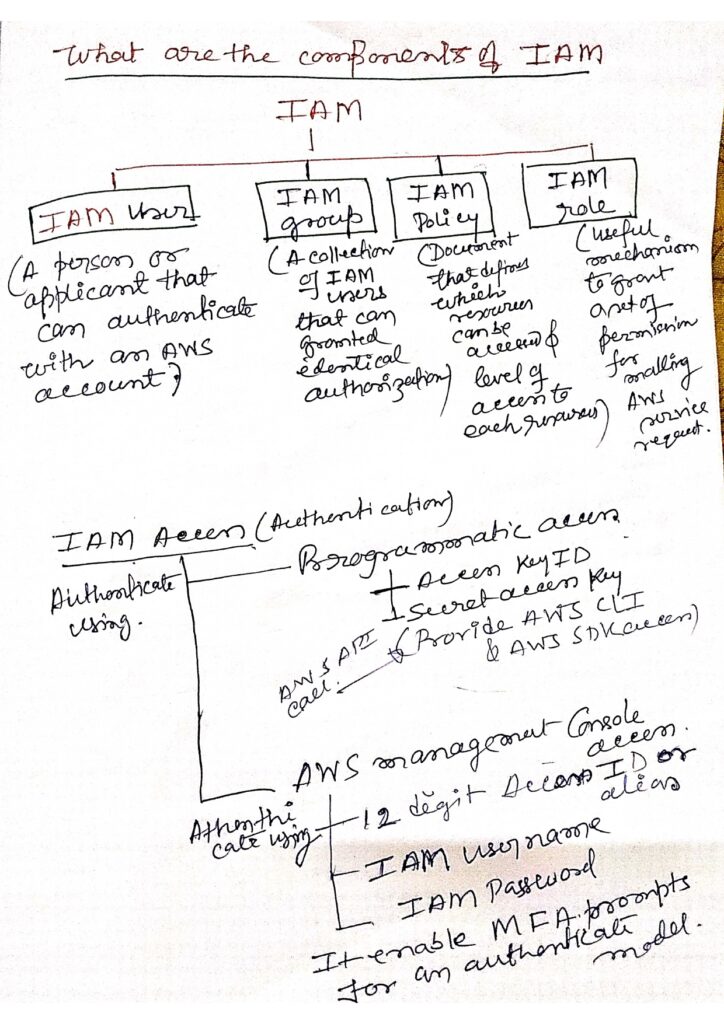


Understanding JSON Policies and Roles in AWS IAM
AWS Identity and Access Management (IAM) is a powerful service that helps you manage access to AWS resources securely. At the heart of this service are policies, typically expressed in JSON format, and roles, which allow you to define permissions for entities like users or applications. This article delves into the intricacies of IAM JSON policies, roles, and the mechanisms behind the permission system that governs access control in AWS.
What is an IAM JSON Policy?
A JSON policy in AWS IAM is a document that defines permissions for an IAM identity (user, group, or role) or an AWS resource. These policies are written in JSON (JavaScript Object Notation), a lightweight data-interchange format that is easy for humans to read and write, and easy for machines to parse and generate.
Structure of a JSON Policy
A JSON policy document is composed of elements that define various aspects of permissions. Here’s a breakdown of a typical policy structure:
- Version: Indicates the language version of the policy. The recommended version is “2012-10-17”.
- Statement: The core component of the policy, which includes:
- Sid (Statement ID): An optional identifier for the policy statement.
- Effect: Specifies whether the statement allows or denies access. It can be either “Allow” or “Deny”.
- Principal: Indicates the entity to which the policy applies. This is only required in resource-based policies.
- Action: Lists the actions that are allowed or denied (e.g.,
s3:ListBucket). - Resource: Specifies the AWS resource to which the actions apply (e.g., an S3 bucket).
- Condition: Optional; allows you to specify conditions under which the policy is in effect, such as requiring multi-factor authentication (MFA).
Example of a Simple JSON Policy
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:ListBucket",
"Resource": "arn:aws:s3:::example_bucket"
}
]
}
This policy allows the entity to list objects in the specified S3 bucket.
Types of IAM Policies
IAM policies can be categorized into several types, each serving a specific purpose:
- Identity-Based Policies: These are attached directly to IAM users, groups, or roles. They define what actions these identities can perform on which resources.
- Resource-Based Policies: These are attached directly to AWS resources like S3 buckets. They define who can access the resource and what actions they can perform.
- Permissions Boundaries: These are advanced policies that set a limit on the maximum permissions an IAM entity can have. They do not grant permissions by themselves but restrict the permissions granted by identity-based policies.
- Service Control Policies (SCPs): Used within AWS Organizations, SCPs define the maximum permissions that identities within an organizational unit (OU) or account can have.
- Access Control Lists (ACLs): Commonly used with Amazon S3, ACLs define which AWS accounts or IAM users can access the resource.
- Session Policies: Temporary policies that are passed when you assume a role or federated user session. They limit the permissions for the duration of the session.
Understanding IAM Roles
An IAM role is an identity in AWS that you can create and assign specific permissions. Unlike a user, a role does not have long-term credentials like a username and password. Instead, a role is meant to be assumed by entities such as users, applications, or other AWS services.
Use Cases for IAM Roles
- Cross-Account Access: Roles can be used to allow access to resources in different AWS accounts. This is particularly useful for scenarios where you need to share resources between accounts securely.
- AWS Service Roles: AWS services like EC2 or Lambda can assume roles to perform actions on your behalf. For example, an EC2 instance might assume a role to access S3 buckets without requiring embedded credentials.
- Federation: Roles can be used to grant temporary access to AWS resources for users who authenticate via an external identity provider, such as Google or Active Directory.
Role Trust Policy vs. Permissions Policy
When creating a role, you must define two key policies:
- Trust Policy (Resource-Based): This policy specifies who (which entities) can assume the role. It is a resource-based policy and must include the principal element to define the trusted entities.Example of a Trust Policy:
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Principal": { "AWS": "arn:aws:iam::account-id:root" }, "Action": "sts:AssumeRole" } ] } - Permissions Policy (Identity-Based): This policy defines what actions the role can perform and on which resources. It is attached to the role and works just like any other identity-based policy.Example of a Permissions Policy
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": "s3:ListBucket", "Resource": "arn:aws:s3:::example_bucket" } ] }
Deny Overrides: The Power of Explicit Denies
In IAM, the most restrictive policy takes precedence. This is important when considering how permissions are evaluated. Even if an allow policy is in place, an explicit deny policy will override it. This mechanism ensures that sensitive operations can be restricted, even if broader permissions are granted elsewhere.
Best Practices for Writing JSON Policies
- Principle of Least Privilege: Always grant the minimum permissions necessary for an entity to perform its tasks. This reduces the potential attack surface.
- Use Managed Policies for Reusability: AWS provides managed policies that can be reused across multiple identities, making management easier and ensuring consistency.
- Implement MFA for Sensitive Actions: Use the Condition element in your policies to enforce multi-factor authentication (MFA) for accessing critical resources.
- Regularly Review Policies: IAM policies should be regularly audited to ensure they are up-to-date and do not grant unnecessary permissions.
- Use Policy Validation Tools: AWS IAM provides tools like policy validation and IAM Access Analyzer, which help identify issues in your policies and suggest improvements
More example of Jason Policy :
Here are some example JSON policies tailored to specific AWS services like EC2, S3, and a mixed scenario.
1. EC2 Instance Policy Example
This policy allows an IAM role to perform actions related to EC2 instances, such as starting, stopping, and describing instances within a specific region.
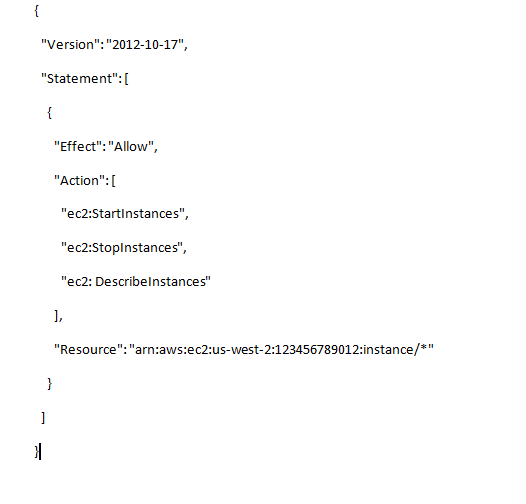
Effect: Allows the specified actions.
Action: Specifies EC2 actions (StartInstances, StopInstances, DescribeInstances).
Resource: Applies to all instances in the specified region (us-west-2).
2. S3 Bucket Policy Example
This policy allows a specific IAM user to upload and download objects from a particular S3 bucket but restricts access to other S3 operations.

Effect: The first statement allows the user to upload and download objects, while the second statement denies deletion of objects and modification of the bucket policy.
Action: Specifies S3 actions like PutObject, GetObject, DeleteObject, and PutBucketPolicy.
Resource: Applies to all objects within the specified S3 bucket (example_bucket).
3. Mixed Policy Example (EC2 and S3)
This policy combines permissions for both EC2 and S3. It allows the role to start EC2 instances and access specific objects in an S3 bucket.

Effect: The policy allows the role to start and describe EC2 instances and access objects in the S3 bucket, but denies the deletion of objects.
Action: Combines EC2 actions (StartInstances, DescribeInstances) and S3 actions (GetObject, PutObject, DeleteObject).
Resource: Targets resources across both EC2 (instance/*) and S3 (example_bucket/*)
AWS IAM Best Practices
AWS Identity and Access Management (IAM) is the cornerstone of securing your AWS environment. By adhering to IAM best practices, you can protect your resources, minimize risks, and ensure that your cloud infrastructure operates smoothly. This guide delves into the most effective strategies to secure your AWS environment using IAM.
1. Use Federation with Identity Providers for Human Users
Federation with identity providers is a key strategy in managing human access to AWS resources. Human users—administrators, developers, and other personnel—require secure access to AWS accounts. Rather than managing long-term credentials directly within AWS, it is recommended to use federated access, which relies on temporary credentials provided by an identity provider.
This method enhances security by reducing the risk of credential leakage or misuse. AWS IAM Identity Center (formerly AWS SSO) is a powerful tool for managing federated access. It allows you to centralize access management across multiple AWS accounts, simplifying the administration of permissions and user roles.
Using IAM Identity Center, you can integrate with external identity providers such as Microsoft Active Directory, enabling single sign-on (SSO) capabilities. This approach ensures that users can access AWS resources without requiring separate credentials, thereby reducing the potential attack surface.
2. Employ Temporary Credentials for Workloads
Workloads, including applications, operational tools, and services, often need to interact with AWS resources. Rather than using static credentials, which pose a security risk if compromised, workloads should use temporary credentials. These can be obtained through IAM roles, which provide a secure and flexible way to grant access to AWS services.
IAM roles allow you to define specific permissions required by your workloads, ensuring they can only perform necessary actions on AWS resources. For instance, an EC2 instance running a backend service might need access to an S3 bucket to store logs. By assigning an IAM role to the EC2 instance, you can grant it the exact permissions it needs, without the risk associated with static credentials.
AWS also offers IAM Roles Anywhere, which extends the benefits of IAM roles to workloads running outside AWS. This feature is particularly useful for on-premises systems or services running in other clouds that need to interact with AWS resources securely.
3. Enforce Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) is an essential security measure that adds an extra layer of protection to your AWS accounts. MFA requires users to provide a second form of verification, such as a one-time code generated by a device, in addition to their password. This significantly reduces the risk of unauthorized access, especially if credentials are compromised.
For scenarios where IAM users or root users need to access AWS, MFA should be mandatory. This is particularly important for root accounts, which have full access to all AWS services and resources. Enabling MFA on root accounts helps prevent unauthorized users from gaining access and potentially causing widespread damage.
IAM Identity Center also supports MFA, making it easy to enforce MFA for users accessing AWS through federated accounts. This integration ensures that all users, regardless of their identity source, must authenticate using multiple factors, thereby strengthening your security posture.
4. Manage Access Keys Responsibly
Access keys are essential for programmatic access to AWS resources. However, they pose a significant security risk if not managed properly. It is recommended to avoid long-term credentials wherever possible, instead relying on temporary credentials obtained through IAM roles. However, in scenarios where long-term credentials are necessary, such as when using third-party AWS clients, it is important to manage access keys carefully.
Regularly rotate access keys to limit the exposure of long-term credentials. This is especially critical when an employee leaves the organization or changes roles. AWS IAM provides tools to help you monitor the last use of access keys, allowing you to identify and deactivate unused or potentially compromised keys.
In cases where long-term credentials are unavoidable, such as with certain third-party tools or AWS services like CodeCommit, make sure to implement stringent monitoring and auditing practices. This ensures that access keys are used securely and only by authorized users or services.
5. Protect Root User Credentials
The root user account is the most powerful account in an AWS environment, with unrestricted access to all resources and services. As such, protecting root user credentials is paramount. Best practices include enabling MFA on the root account, using the root account only for essential tasks, and creating individual IAM users for day-to-day operations.
Storing root credentials securely, preferably using a hardware security module (HSM) or an encrypted vault, further reduces the risk of unauthorized access. Regularly reviewing and limiting the actions performed with the root account also contributes to a more secure AWS environment.
6. Apply Least-Privilege Permissions
Least-privilege permissions are a fundamental principle in IAM. This involves granting users, roles, and services only the permissions they need to perform their tasks, and nothing more. This approach minimizes the risk of accidental or intentional misuse of AWS resources.
To implement least-privilege permissions effectively, start with broad permissions and gradually refine them based on the actual needs of your workloads or users. AWS IAM policies should be carefully crafted to specify the actions that can be performed on specific resources under defined conditions.
Using AWS Managed Policies is a good starting point for granting permissions. These policies are designed for common use cases and can help you avoid the complexities of writing custom policies from scratch. However, AWS Managed Policies may not always grant the minimum required permissions, so it’s important to review and adjust them as necessary.
7. Leverage IAM Access Analyzer
IAM Access Analyzer is a powerful tool that helps you identify and mitigate security risks in your IAM policies. It can analyze your IAM environment to generate least-privilege policies based on actual access patterns, ensuring that you only grant the permissions that are truly needed.
IAM Access Analyzer also provides continuous monitoring of your IAM resources, alerting you to any potential security issues such as excessive permissions or public access. By regularly using IAM Access Analyzer, you can maintain a secure IAM environment and adhere to the principle of least privilege.
8. Regularly Review and Clean Up IAM Resources
Over time, your AWS environment may accumulate unused IAM users, roles, permissions, and policies. These unused resources can become security liabilities if not properly managed. Regularly reviewing and removing unused IAM resources is a best practice that helps maintain a secure and organized IAM environment.
AWS provides tools to help you identify unused resources, such as the “last accessed” information for IAM users and roles. By leveraging this information, you can safely deactivate or delete unused resources, reducing the potential attack surface of your AWS environment.
9. Use Conditions in IAM Policies
Conditions in IAM policies allow you to specify additional constraints on when and how permissions can be used. For example, you can enforce that certain actions can only be performed from specific IP addresses or that requests must be made over SSL. Using conditions adds an extra layer of security, ensuring that even if permissions are granted, they can only be used under specific, controlled circumstances.
Conditions can be particularly useful in scenarios where you need to grant broad permissions but want to ensure they are only used in a secure context. For example, allowing S3 bucket access only from within your corporate network adds a layer of security against external threats.
10. Establish Permissions Guardrails Across Accounts
As your organization grows, it may become necessary to manage multiple AWS accounts. Using AWS Organizations, you can establish service control policies (SCPs) to enforce permissions guardrails across all accounts. SCPs allow you to define what actions can and cannot be performed within an account, ensuring consistent security policies across your organization.
SCPs are not a replacement for IAM policies but work in conjunction with them to provide an additional layer of control. By carefully designing SCPs, you can ensure that all accounts in your organization adhere to your security standards, regardless of individual IAM policies.
11. Delegate Permissions Management with Boundaries
In some scenarios, it may be necessary to delegate permissions management to other users within an account. Permissions boundaries are a tool that allows you to delegate permissions management while still maintaining control over the maximum permissions that can be granted.
Permissions boundaries set a cap on the permissions that can be granted to a user or role, ensuring that even if they have the ability to create or modify IAM policies, they cannot exceed the predefined limits. This is particularly useful in environments where developers or other personnel need to manage their own permissions without compromising overall security.
Conclusion
Implementing these best practices in AWS IAM is crucial for maintaining a secure and well-managed cloud environment. By focusing on temporary credentials, enforcing MFA, protecting root user access, and regularly reviewing your IAM resources, you can significantly reduce security risks. Furthermore, leveraging tools like IAM Access Analyzer and IAM Identity Center will help you maintain a robust and secure IAM strategy that evolves with your organization’s needs.
4o